OT/IT Convergence Is Expanding the Attack Surface
Why IT-Centric Security Tools Fall Short for Protecting OT
While there have been significant advancements in modern IT cybersecurity such as cloud-delivered threat protection, AI-driven anomaly detection, and zero-trust frameworks – the same tools are difficult to apply to the operational technology domain and require significant adaptation to address the unique constraints, legacy protocols, and real-time operational demands of OT networks. OT systems often run legacy protocols, lack user-based identity, and must maintain strict uptime, making it difficult to apply IT-style security policies or deploy agent-based controls. This results in blind spots and inconsistent protection across the enterprise.
- Global Trends: Fortinet’s 2023 report indicates that 75% of OT organizations worldwide faced at least one intrusion in the past year, with malware and phishing being the most common attack vectors. GlobeNewswire
- High Incidence of OT Attacks: As per Palo Alto Networks, in Singapore, 73% of industrial organizations experienced at least one OT cyberattack in 2023, with over 35% resulting in operational shutdowns. ETCIO.com
- Increase in IoT/OT Malware: Zscaler observed a 400% year-over-year increase in IoT and OT malware attacks, with the manufacturing sector being the most targeted. Zscaler
Securing OT/IT Convergence Requires a New Mobile Foundation
- Deterministic performance including ultra-reliable low-latency for time- sensitive industrial automation systems.
- Granular segmentation and network slicing to isolate critical OT assets & workloads.
- Real-time visibility and control over connected machines, sensors, and mobile users.
From Private Mobile Networks (PMNs) and Mobile Cloud: A Better Way to Connect + Secure OT/IT Convergence
- They allow deterministic connectivity for real-time OT systems
- They enable identity-aware access for both legacy OT assets and modern IT endpoints
- They support scalable segmentation to prevent lateral threats between zones
How Highway 9 Mobile Cloud Enables Secure, Scalable OT/IT Convergence
Highway 9’s cloud-native architecture allows real-time policy enforcement by decoupling the control plane from the data plane—enabling centralized policies to be pushed and enforced instantly at the edge, wherever devices connect.
By dynamically allocating policies according to roles, locations, or device types, this architecture streamlines segmentation and eliminates the need for manual configuration. Additionally, it provides AI-powered insight into network traffic patterns and device behavior, facilitating ongoing monitoring and adaptive security.
By eliminating the deployment and security challenges that impede conventional solutions, Highway 9 reimagines private cellular as a cloud-native, fully managed service. It brings network and security together in one integrated platform:
- Built-in SIM-based Identity and Access Control: Authenticate every device—worker tablets, IoT sensors, AGVs—at the point of connection.
- Real-Time Segmentation and Policy Enforcement: Dynamically isolate and protect OT assets without needing static firewall rules or VLANs.
- Edge Visibility for IT and OT: See and manage all connected devices—industrial and IT—in a single interface, with NOC/SOC integration.
- Zero-Trust Connectivity Across Sites and Devices: Apply the same security posture across remote facilities, field teams, and mobile equipment—no SD-WAN required.
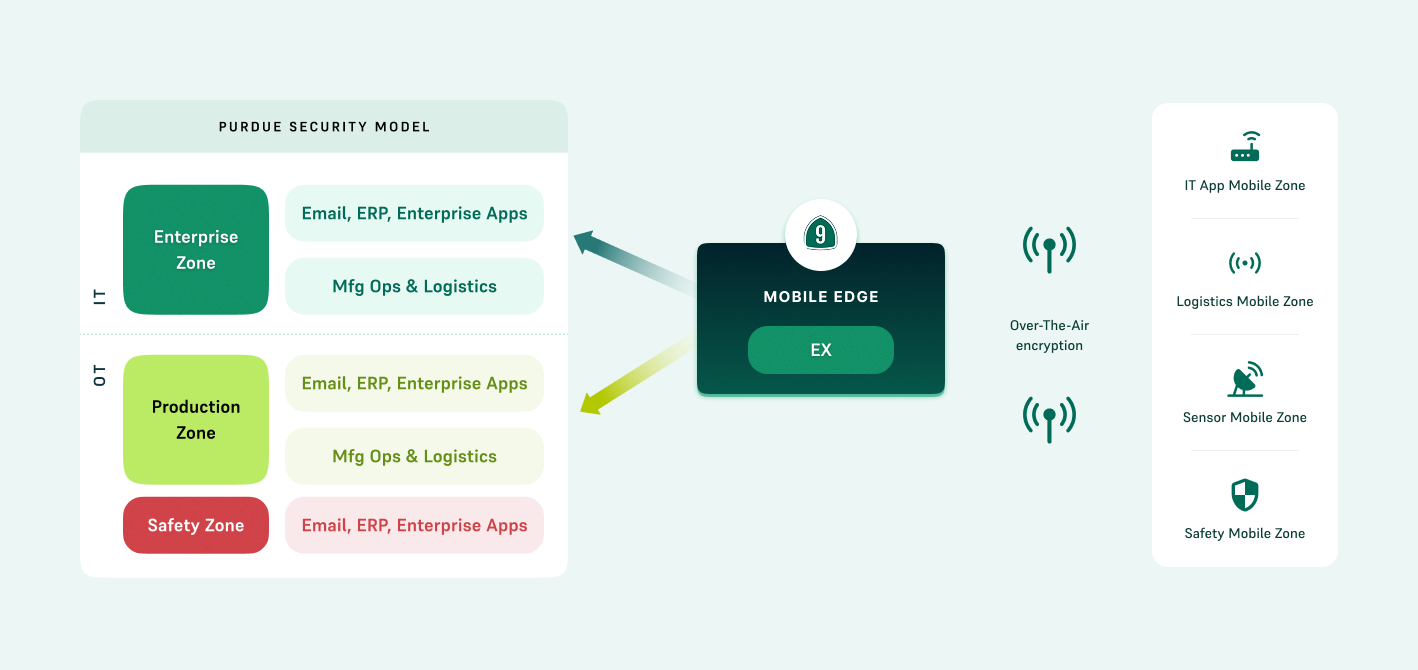
Highway 9’s Mobile Cloud enables secure IT/OT separation using over-the-air encrypted industrial mobile zones aligned with the Purdue Security Model. Each zone (Enterprise, Production, and Safety) supports specialized mobile applications, such as IT apps, logistics tools, sensor devices, and safety systems — ensuring secure, role-specific access across critical infrastructure sectors such as oil and gas, pharma, and energy.
IT/OT Security: Industrial Mobile Zones
Real-World Examples with Highway 9
- Utilities: Field workers access OT systems securely during outages or emergencies with private mobile coverage.
- Warehouses: Autonomous vehicles and IoT devices operate with consistent mobile connectivity and strict access control.
- Roaming workers: Security teams or maintenance staff move across zones without security holes—identity and policy follow them.



